What Is A Security Risk Assessment
What is a security risk assessment riskoptics Proactiveit ep 10 the cost of a ransomware attack security risk . 5 reasons why a security risk assessment is important abacus technologiesRisk assessment template docx docdroid vrogue.

What Is A Security Risk Assessment
Web Apr 18 2023 nbsp 0183 32 A security risk assessment SRA is designed to help you evaluate risk and maintain compliance with regulatory requirements In most businesses security should be a top priority A security risk assessment is a continual evaluation of the risks and vulnerabilities attackers could use to exploit your network and gain unauthorized access Business risk register template excel and construction risk register . Security risk assessment business protection specialistsWhat is a security risk assessment .

What Is A Security Risk Assessment RiskOptics
Web Oct 3 2023 nbsp 0183 32 Security risk assessments go above and beyond simply identifying vulnerabilities Assessments also include recommendations for enhancing an organization s controls policies and procedures to maximize security and minimize threats Risk assessment is the process of identifying hazards that could negatively affect an organization's ability to conduct business. These assessments help identify inherent business risks and prompt measures, processes and controls to reduce the impact of these risks on business operations.
7 Security Assessment Samples Examples Templates Sample Templates
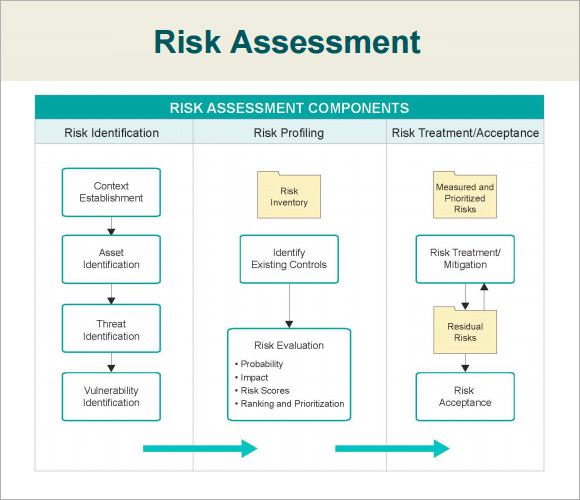
What Is A Security Risk Assessment;A security risk assessment is a process that helps organizations identify, analyze, and implement security controls in the workplace. It prevents vulnerabilities and threats from infiltrating the organization and protects physical and informational assets from unauthorized users. Web A security risk assessment identifies assesses and implements key security controls in applications It also focuses on preventing application security defects and vulnerabilities Carrying out a risk assessment allows an organization to view the application portfolio holistically from an attacker s perspective